TrialKit is able to enforce specific email domains to use their own company’s SSO provider (IdP) as an added security mechanism beyond the traditional username/password specific to TrialKit. Current supported IDPs include:
OKTA
Ping Identity
When a domain is registered by an Administrator to use SSO, any user with that domain who attempts to log in directly to TrialKit will be redirected to the SSO sign in connected with their domain. Manual login with a TrialKit-based password will be prevented and the user will not be able to rest their login (retrieve forgotten password) from TrialKit.
To request your Company domain to be enforced for SAML SSO, a current study Administrator should send the following information in a support request:
Domain name where SSO will be forced
Login URL/Endpoint - This is generated when creating an application in the IdP
Base64 certificate - This is generated when creating an application
To get that information from the domain owner or IT Administrator, they will need to create an application with the following information:
Entity ID - <domainName>TKSSO (for example: MyCompanyTKSSO)
Return URLs (Assertion Consumer Service URL) for the Domain Administrator to log with the SSO provider:
https://webapp-eu.trialkit.com/pages/Saml_callback.aspx?domain=DOMAINNAME
https://www.trialkit.com/Pages/Saml_callback.aspx?domain=DOMAINNAME
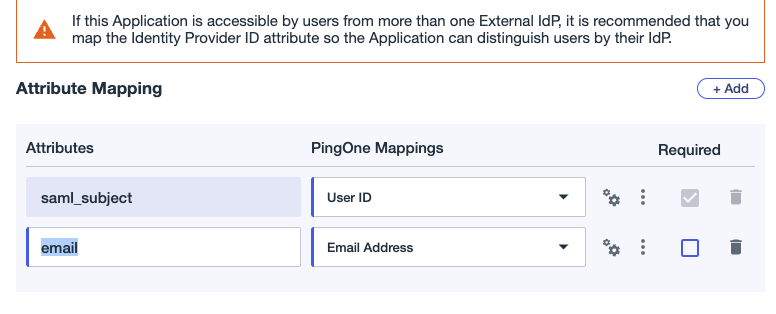
Lastly, some IdPs require an attribute the user email to be set as an attribute like this: